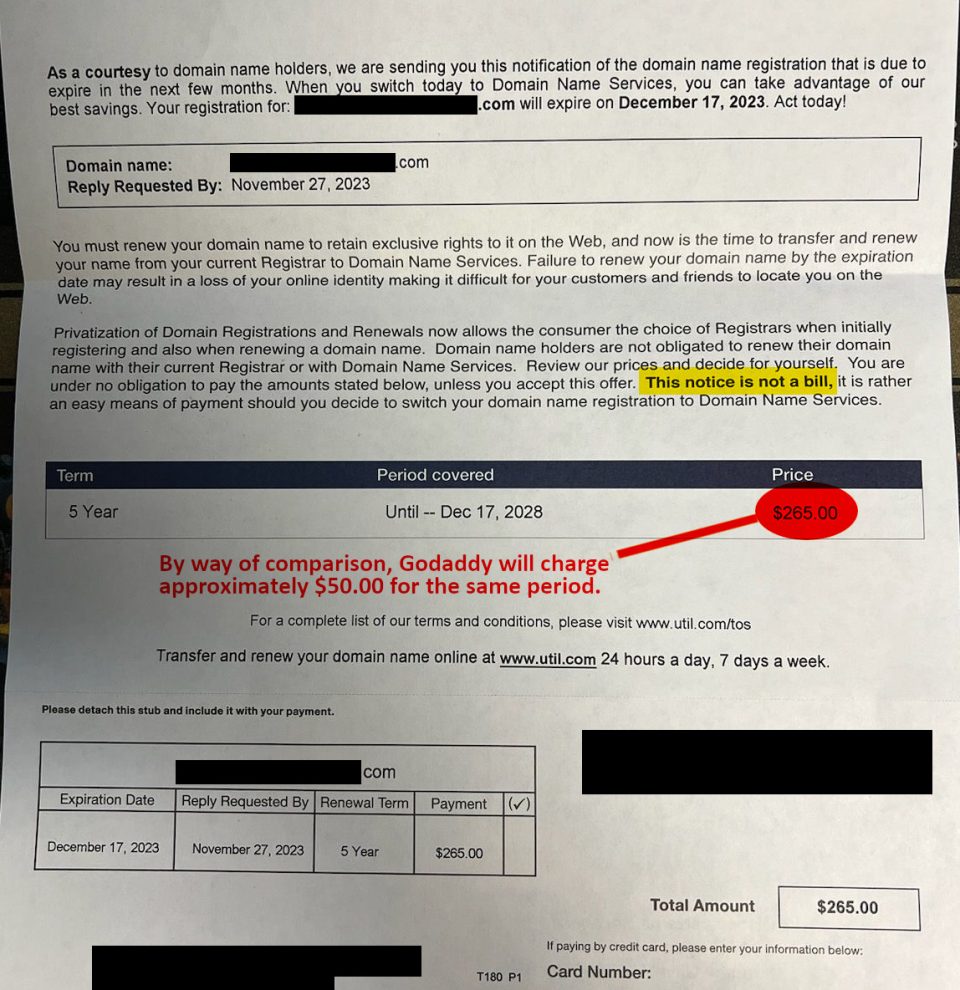
Two unpatched exploits have appeared this week and many warn that one of them is particularly serious. It can be executed by simply viewing an infected HTML email in Outlook 2003.
“The newest exploit works with e-mail,” said Ken Dunham, the director of iDefense’s rapid response team. “We took the newest version of Outlook, all patched, and the exploit crashed it.” With some help from iDefense researchers, however, the exploit was able to execute other code. That means e-mail clients that preview HTML messages using the IE rendering engine are at risk. Just previewing a message could result in a computer hijacked by a bot or loaded with adware, spyware, or other malicious code.
“You would be attacked immediately, as soon as the preview is rendered,” said Dunham.
This means that as soon as you view an HTML email (one with images that automatically show up) that is infected, you are infected. You do not have to actually click on anything in the email or visit a web site or anything. You are infected.
We released a tip explaining a simple way to have a very small measure of protection by turning off your email preview option in Outlook and Thunderbird. But that is not foolproof. Hopefully, Microsoft will release a patch, but they gave no indication that they would do so prior to the next scheduled patch date of October 12, 2006.