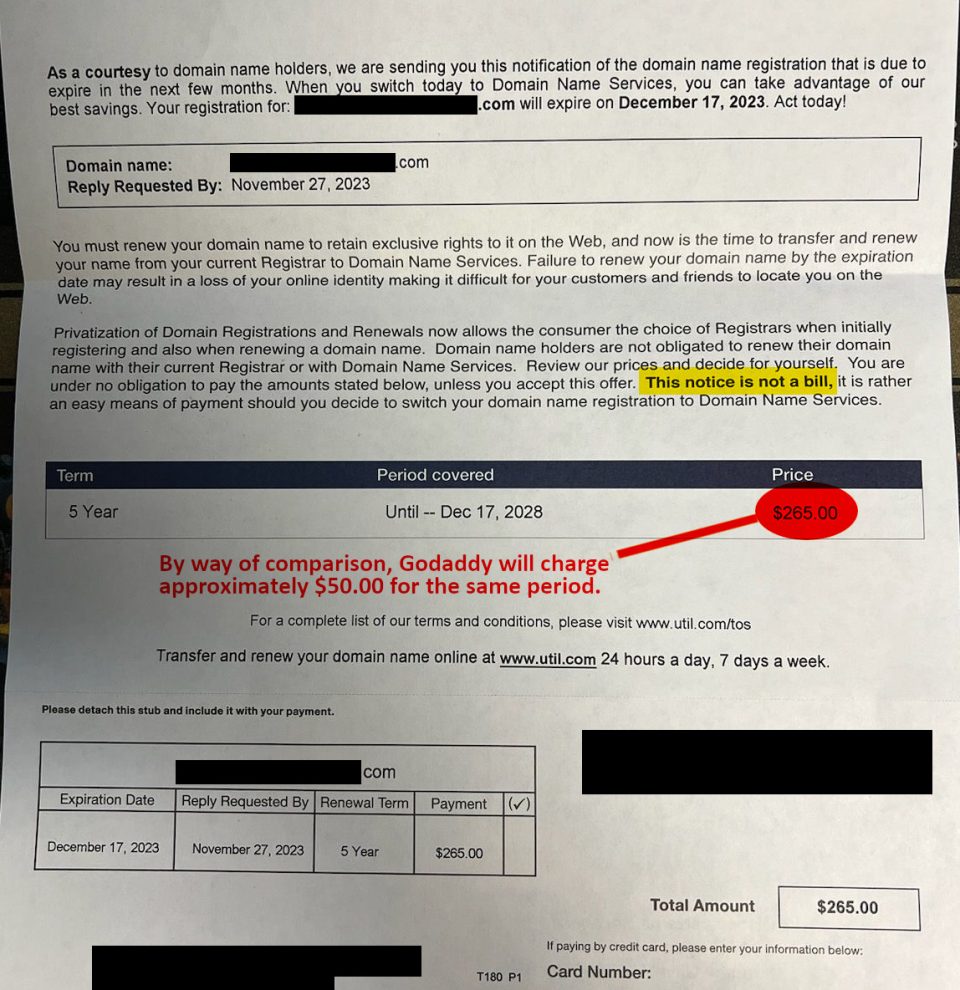
from e-week
Microsoft’s dominant Internet Explorer browser has undergone a major security makeover to plug 10 vulnerabilities that puts millions at risk of PC takeover, address bar spoofing and information disclosure attacks.
The monster IE update includes a fix for the “createTextRange()” code execution flaw that caused zero-day drive-by downloads and a significant modification to the way the browser renders certain ActiveX controls.
In all, Microsoft shipped five bulletins with patches for 14 different vulnerabilities in a range of Windows products.
Three the five bulletins are rated “critical,” the company’s highest severity rating.
In addition to the IE update, critical bulletins were issued for a code execution bug in the MDAC (Microsoft Data Access Components Function) in Windows and a remotely exploitable flaw in Windows Explorer.
Microsoft recommends that Windows users treat the MS06-013 bulletin as a high-priority update to protect against an active attack vector that used social engineering tricks to lure IE users to Web sites rigged with bots, spyware, back doors and other Trojan downloaders.
The IE update applies to users of Windows 2000 (SP4 only), Windows XP (SP1 and SP2), and Windows Server 2003 (including SP1).
Customers running Windows 98, Windows Millennium Edition and Windows 2000 (pre SP4) are affected, but because these operating systems are out of mainstream lifecycle support, there are no free patches.
Those users must pay for custom support to get protection, Microsoft said in the FAQ section of the bulletin.
The MDAC flaw, covered in MS06-014, is described as a remote code execution issue in the RDS.Dataspace ActiveX control.
An attacker who successfully exploits this vulnerability “could take complete control” of an affected system, Microsoft said.
The third “critical” bulletin (MS06-015) also puts users at risk of PC takeover attacks.
Microsoft said the vulnerability exists in Windows Explorer because of the way that it handles COM objects.
“An attacker would need to convince a user to visit a Web site that could force a connection to a remote file server. This remote file server could then cause Windows Explorer to fail in a way that could allow code execution,” the company said.
The April security updates also include:
A new version of the company’s malicious software removal tool was also released to add signatures to detect and remove Win32/Locksky, Win32/Valla, Win32/Reatle.
If you are interested in using a different web site browser, read our post about Firefox here.